Nft Add Rule
Nft add rule filter input ip saddr { 10.0.0.0/8, 192.168.0.0/16 } tcp dport { 22, 443 } accept named sets are sets that need to be defined first before they can be referenced in rules. Using this table it's possible to add only one rule and match both protocols (in case of udp and tcp).

Securing Your Server With Nftables Datapacketcom
Configure also to allow established connections.

Nft add rule. Root@host:~# nft add rule inet filter input tcp dport {80, 443} ct state new,established counter accept delete delete rule with. The total sales volume for rule completion add was $0. % nft add rule nat postrouting ip saddr 192.168.1.0/24 oif eth0 snat to 1.2.3.4 this matches for all traffic from the 192.168.1.0/24 network to the interface eth0.
Nft add rule filter output ip 10.1.1.1 tcp dport ssh accept # handle 5 # delete the rule with handle 5 for port 22 to port 2222 add rule nat 24/12/2017 · therefore, for example, if a rule rejecting ssh connections is created, to add other ports, specify one port or a port range, Root@localhost ~ # nft add rule inet filter output ip daddr 8.8.8.8 counter. To add new rules, you have to specify the corresponding table and the chain that you want to use, eg.
For example, to add a rule to the example_chain in the example_table that allows tcp traffic on port 22: Set your own minting fees, and perform air drops easily. The ssh rule is at handle 4 so adding to position 4 will add after the ssh rule :
Add a new rule to accept several tcp ports: Root@host:~# nft add rule inet filter input tcp dport 22 counter. Configure rarity, mint fees and more.
The ipv4 address 1.2.3.4 is used as source for the packets that match this rule. To add the new rule before position 3, replace add with insert. Create rule which allow ssh and count input traffic :
Named sets are sets that need to be defined first before they can be referenced in rules. ) shifting token add (: Notice the inetprefix before the table name (filter).
Sets are referenced from rules using an @ prefixed to the sets name. Unlike anonymous sets, elements can be added to or removed from a named set at any time. ) stack now 0 entering state 1 reading a token:
Outbound connections are allowed for all interfaces. } # allow lan to firewall, disallow wan to firewall chain input { type filter hook input priority 0; Sudo nft list table inet example_table similarly, you can use a command like the example to list all of the rules within.
Iifname lan0 accept iifname wan0 drop } # allow packets from lan to wan, and wan to lan if lan initiated the. That's the table's family type. Nftables adds in addition to protocol specific tables ”ip” (ipv4) and ”ip6” (ipv6) support for a ipv4/ipv6 aware table named ”inet”.
To add a new rule, use the nft add rule command. Add a nat rule to translate all traffic from the 192.168.0.0/24 subnet to the host's public ip: Sudo nft add rule inet example_table example_chain position 3 tcp dport 22 counter accept you can use a command like the example to list all chains and rules living in the example_table:
Unlike anonymous sets, elements can be added to or removed from a named set at any time. Nft add rule filter input ip saddr { 10.0.0.0/8, 192.168.0.0/16 } tcp dport { 22, 443 } accept. Instead of the port number, you can alternatively specify the name of the service.
Create rule which allow web protocols for new or established states and count input traffic : 0 rule completion add nfts were sold in the last 7 days. Nft add rule inet filter input iif lo accept nft create rule inet filter input ip saddr 127.0.0.0/8 counter drop nft add rule inet filter input ip6 saddr ::1 counter drop.
Sets are referenced from rules using an @ prefixed to the sets name. % nft add rule filter output ip daddr 8.8.8.8 counter where filter is. # nft add rule inet example_table example_chain tcp dport 22 accept.
Configure how rare each layer of an nft is. ) entering state 19 reading a token: Iif lo accept # handle 2 ct state established,related accept # handle 3 tcp dport ssh accept # handle 4 tcp.
Sudo nft add rule nat postrouting ip saddr 192.168.0.0/24 masquerade. Add custom metadata, configure different game rules.
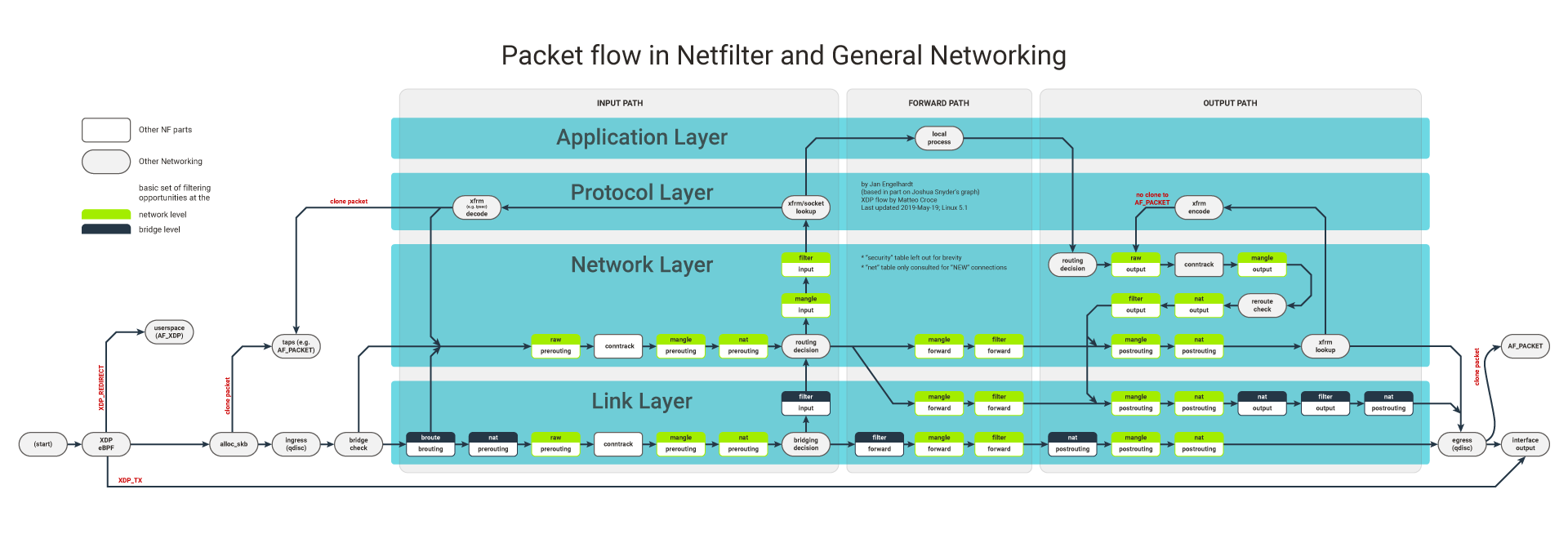
How To Drop A Packet In Linux Iptables Ebtables Nftables And More - Codilime
Cryptopunks And Bored Apes Rule New Index Fund For Nft Blue Chips - The Defiant

How To Setup Router On Red Hat 8 With Nftables - Youtube
Netfilter Libnl-nftsrcnf-rule-addc File Reference

Usdt Airdrop Starts Das Binance Nft Premium Bit Accounts Auctions By Dasystems Medium

Monitoring Ruleset Varshas Blog
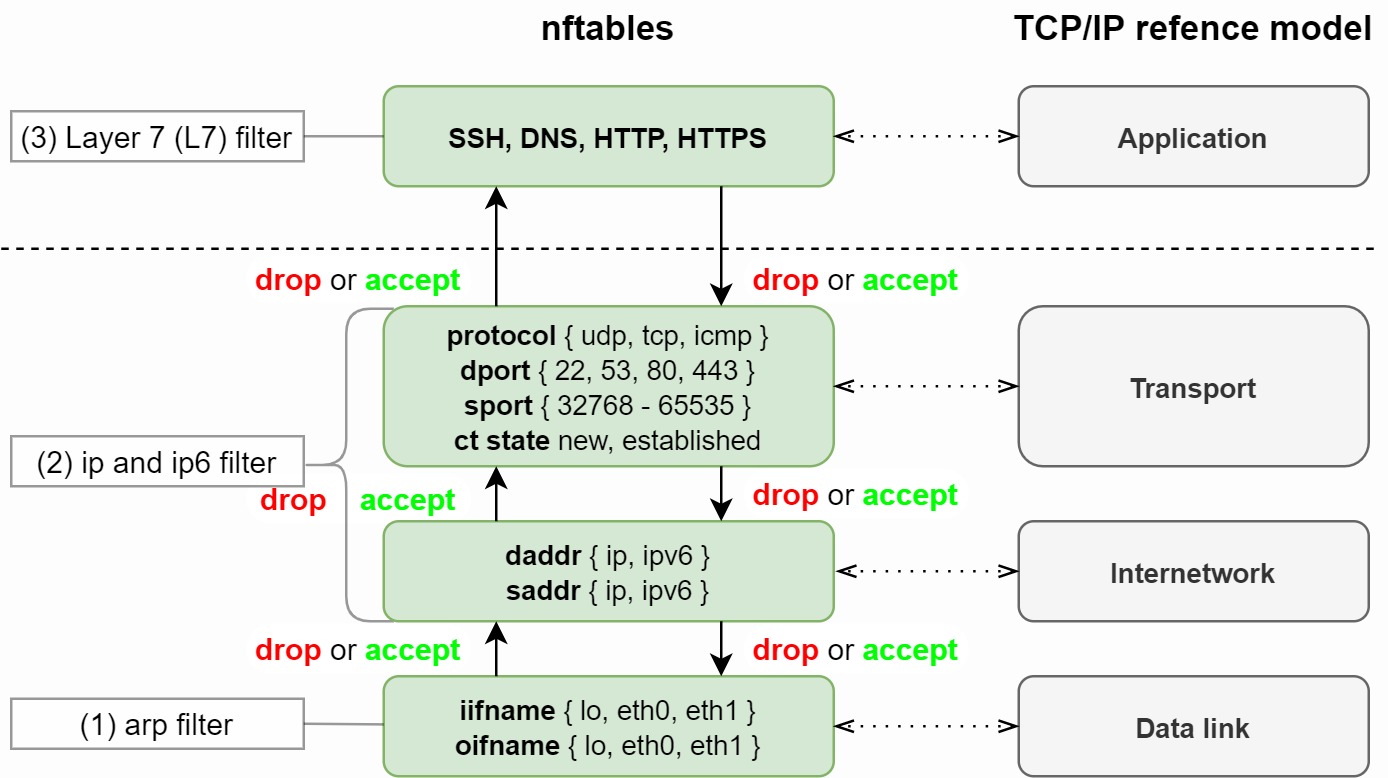
Setting Up Nftables Firewall Cryptsus Blog

Netfilter Framework Providing Hooks System For Nftables
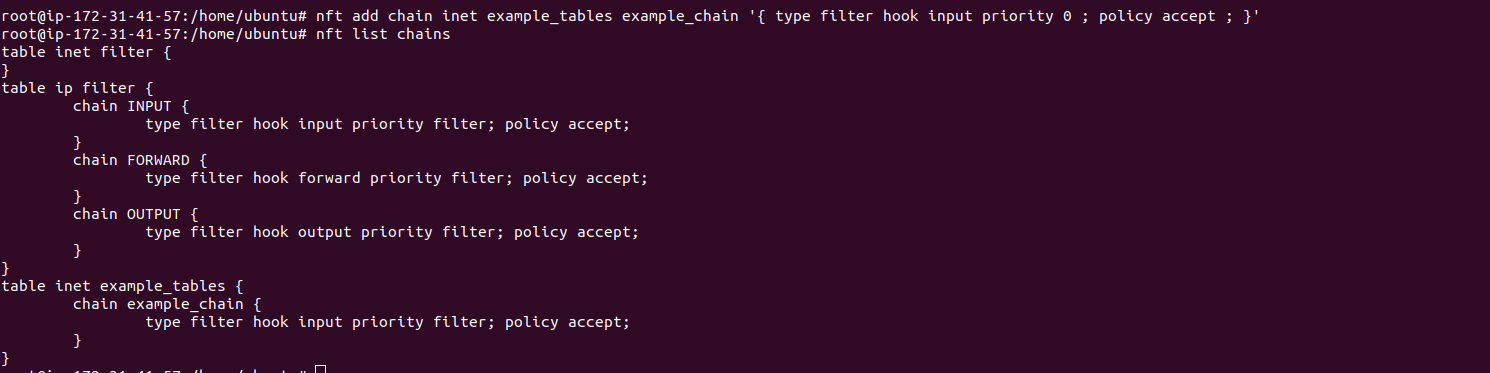
How To Install Nftables On Ubuntu 2004 Lts

Nft Generator Tool - For Solana Nft Art Projects Nova Launch
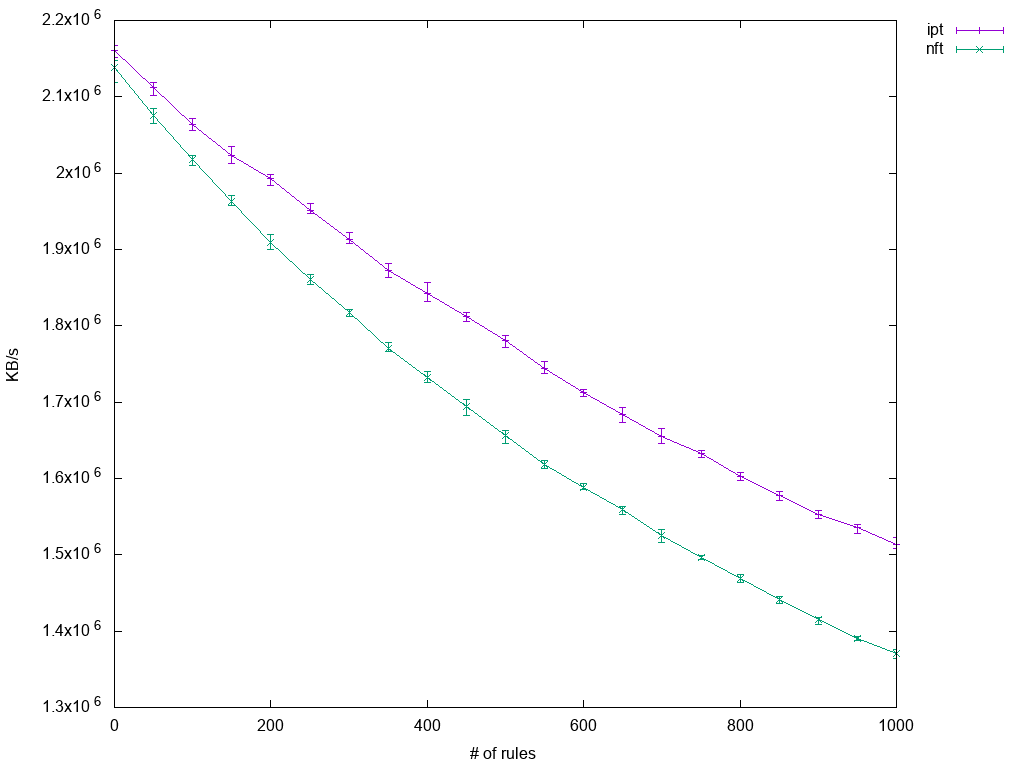
Benchmarking Nftables Red Hat Developer

What Is The Nft Rule To Let Ssh Tunnel To Work - Stack Overflow

Linux Nftables Overview - Speaker Deck

Nftables - The Evolution Of Linux Firewall

Nftables - The Evolution Of Linux Firewall

Learning About Nftables My Technical Blog
Nftables 2 Basic Ruleset Design - Computer Outlines Blog

