Linux Nft Show Rules
Arptables is a user space tool, it is used to set up and maintain the tables of arp rules in the linux kernel. It does not assume complete control of the firewall's backend and will not delete firewall rules installed by other tools or users.
How To Install Nftables On Ubuntu 2004 Lts
The fifth example shows how nftables can be combined with bash scripting.

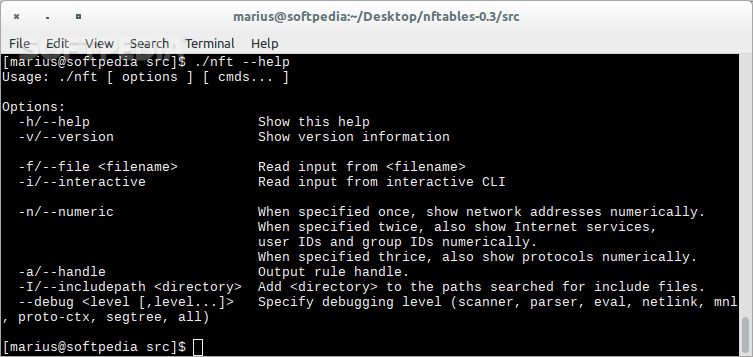
Linux nft show rules. When used once (the default behaviour), skip lookup of addresses to symbolic names. In nftables, they are optional and must be specified. You can list the rules that are contained by a table with the following command:
Chains the kernel table is used to divide functionality into different sets of rules. Nft flush table mytable to delete a table (which also empties it first). Nft flush chain mytable mychain to delete a chain (ditto).
Nft is the command line tool used to set up, maintain and inspect packet filtering and classification rules in the linux kernel, in the nftables framework. Nftables has options built in for exporting your configuration. The packet and byte counters are also listed, with the suffix ‘k’, ‘m’ or ‘g’ for 1000, 1,000,000 and 1,000,000,000 multipliers respectively.
Nft is the command line tool used to set up, maintain and inspect packet filtering and classification rules in the linux kernel, in the nftables framework. [root@localhost ~]# nft add rule inet my_table my_filter_chain tcp dport ssh accept rules are deleted with the help of rule handles. The linux kernel subsystem is known as nf_tables, and 'nf' stands for netfilter.
Linux iptables list and show all nat iptables ipv6 rules command Ip daddr 8.8.8.8 counter packets 0 bytes 0. This option makes the list command show the interface name, the rule options (if any), and the tos masks.
Flush and delete all nftables rules, chains and tables # nft=/usr/bin/nft: Nft add rule address_family my_table my_filter_chain tcp dport ssh accept example: The linux kernel subsystem is known as nf_tables, and ‘nf’ stands for netfilter.
Nft is used to set up, maintain and inspect packet filtering and classification rules in the linux kernel. And it was saved right in place/. Now list you tables and take a look on how things are going.
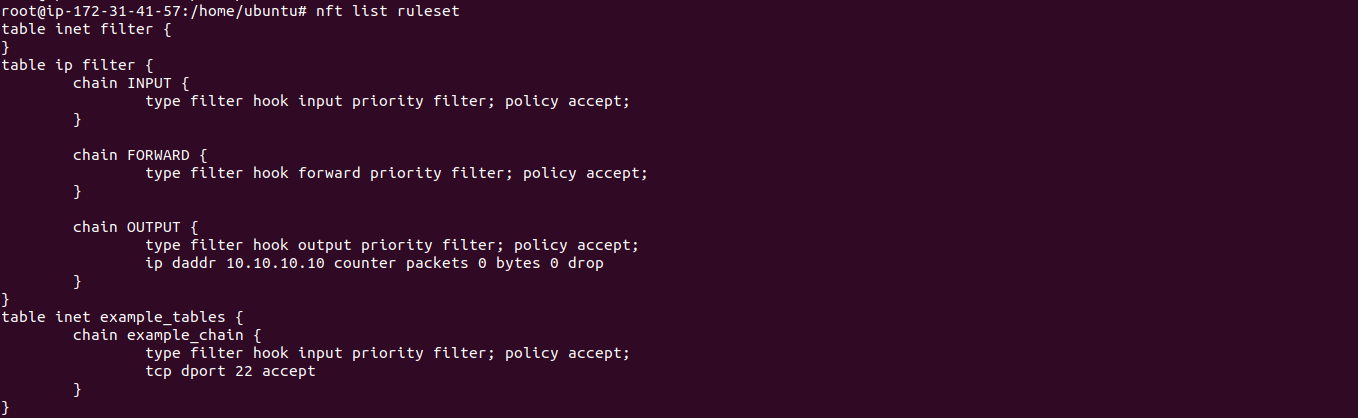
Sudo nft list ruleset > /etc/nftables.conf. The linux kernel subsystem is known as nf_tables, and ‘nf’ stands for netfilter. Most linux systems runs openssh, it is a good idea to accept connections to the tcp port 22, so you can access your ssh service.
Tcp dport 22 accept # handle 2 tcp dport 443 accept # handle 3 tcp dport 389 accept # handle 4 } } How is the new way to view firewall activity with this nftables system? In reality you for sure will add a more complex set of rules.
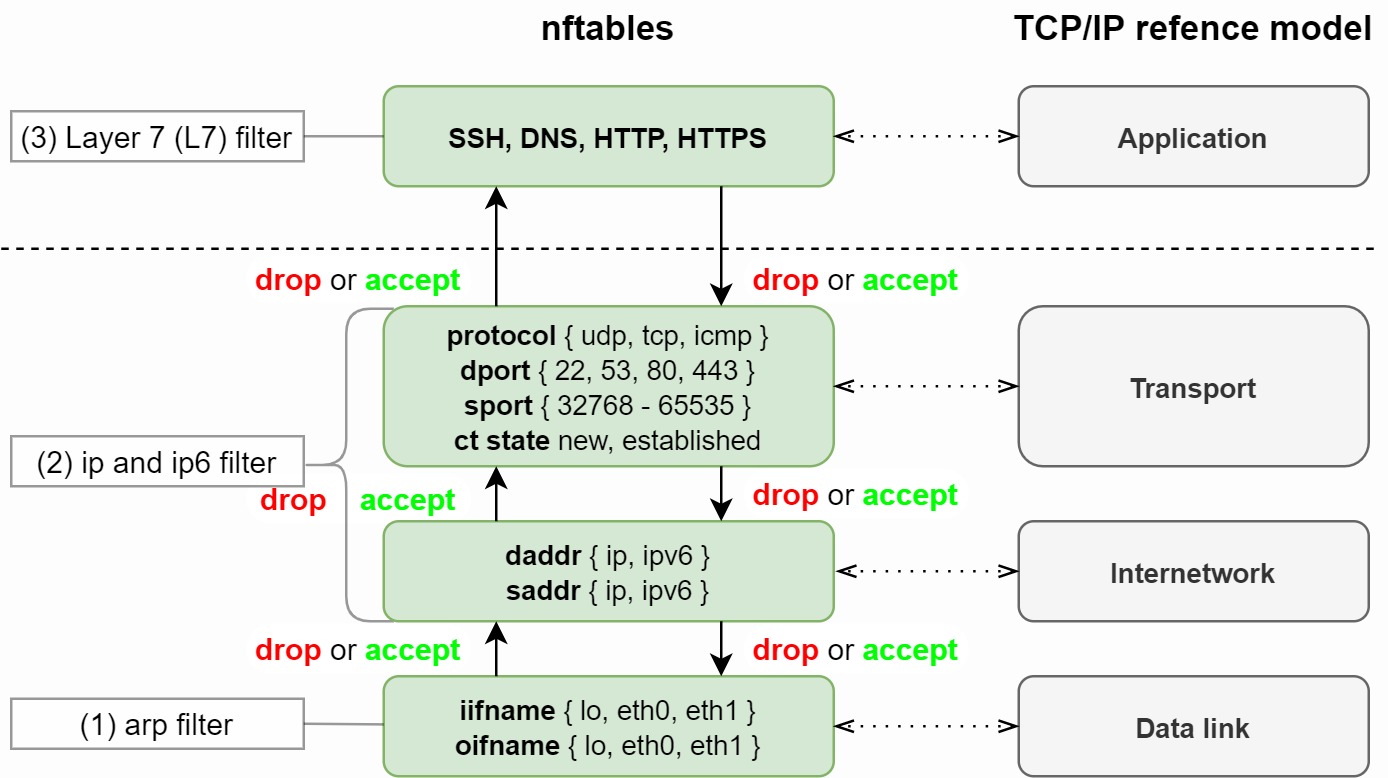
You can also list rules by chain, for example: These rules inspect the arp frames which they see. But when i reboot my nftables rules and tables dissapiered!
Arptables is analogous to the iptables user space tool, but arptables is less complicated. Families= ip ip6 arp bridge for family in $families; Lastly, the new nft backend is nearly 100% compatible with preexisting firewall configurations.
% nft list chain filter ouput table ip filter { chain output { type filter hook output priority 0; The first two examples are skeletons to illustrate how nftables works. The third and fourth exmaple show how, using nftables, rules can be simplified by combining ipv4 and ipv6 in the generic ip table 'inet'.
Nft also improves the firewall ruleset by adding in the options for logging and deny functions in the same rule. To delete a rule, you must find the handle of the rule you want to delete. Nft add rule ip filter input ip saddr 192.168.2.1 counter accept.
Addresses and other information that might need network traffic to resolve to. Nft flush ruleset to empty a table (with ip as family by default if not specified). Nft insert rule filter input tcp port 22 accept.
Nft add rule filter input ct state related,established accept. On this page several example nftable configurations can be found. Nft is the command line tool used to set up, maintain and inspect packet filtering and classification rules in the linux kernel, in the nftables framework.
Nft create table ip nat nft create chain ip nat postrouting {type nat hook postrouting priority srcnat\;} nft add rule ip nat postrouting oif eth1 masquerade nft create table ip filter nft create chain ip filter input {type filter hook input priority filter\;} nft create chain ip filter forward {type filter hook forward priority filter\;} nft. Set up, maintain and inspect packet filtering and classification rules in the linux kernel, in the nftables framework. Nft delete table mytable to empty a chain (ditto).
The “counter” option present in the nft command examples above tells nftables to count the number of times a rule is touched, like iptables used to do by default.

Additional Filters Via Nftables
Netfilter Iptablesiptablesnfth File Reference

Additional Filters Via Nftables

Unifying Network Filtering Rules For The Linux Kernel With Ebpf
Setting Up Nftables Firewall Cryptsus Blog

Securing Your Server With Nftables Datapacketcom

Using Nftables In Red Hat Enterprise Linux 8 - Progworld

Beginners Guide To Nftables Traffic Filtering - Linux Audit
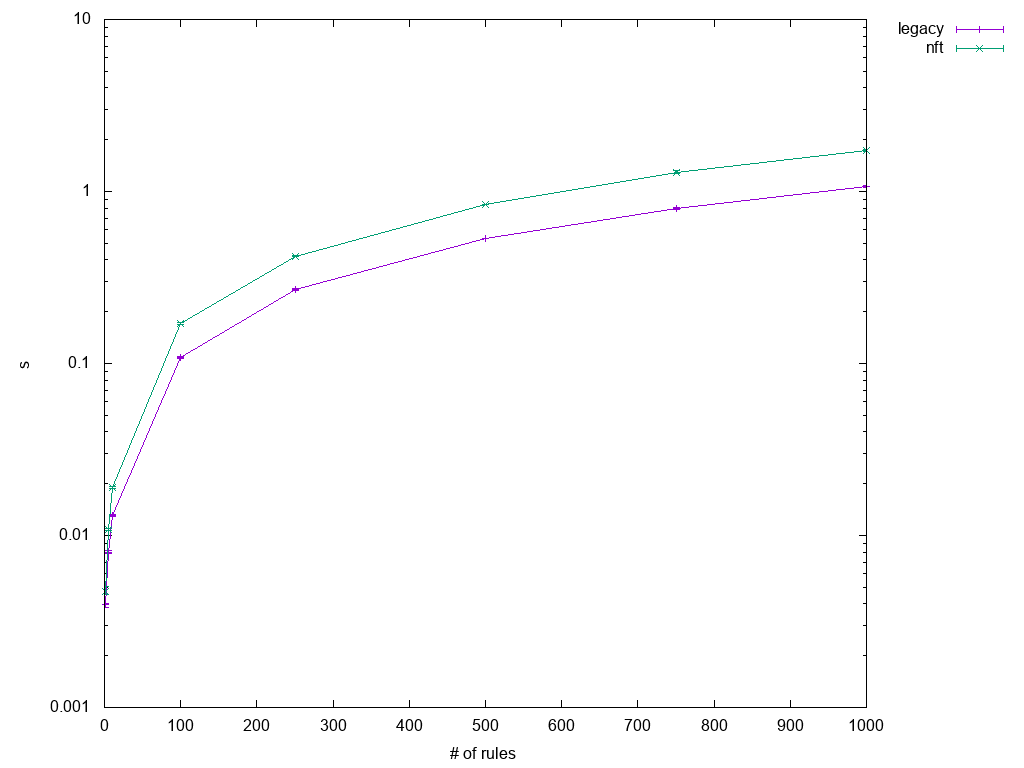
Optimizing Iptables-nft Large Ruleset Performance In User Space Red Hat Developer

Beginners Guide To Nftables Traffic Filtering - Linux Audit
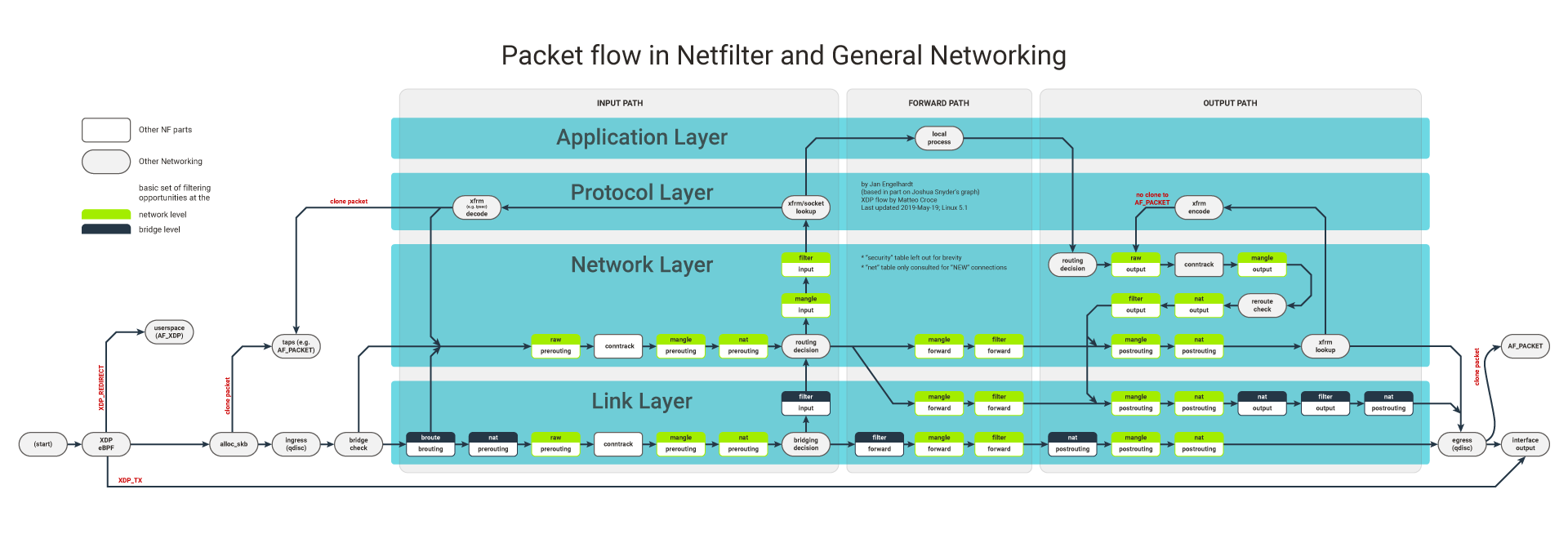
How To Drop A Packet In Linux Iptables Ebtables Nftables And More - Codilime
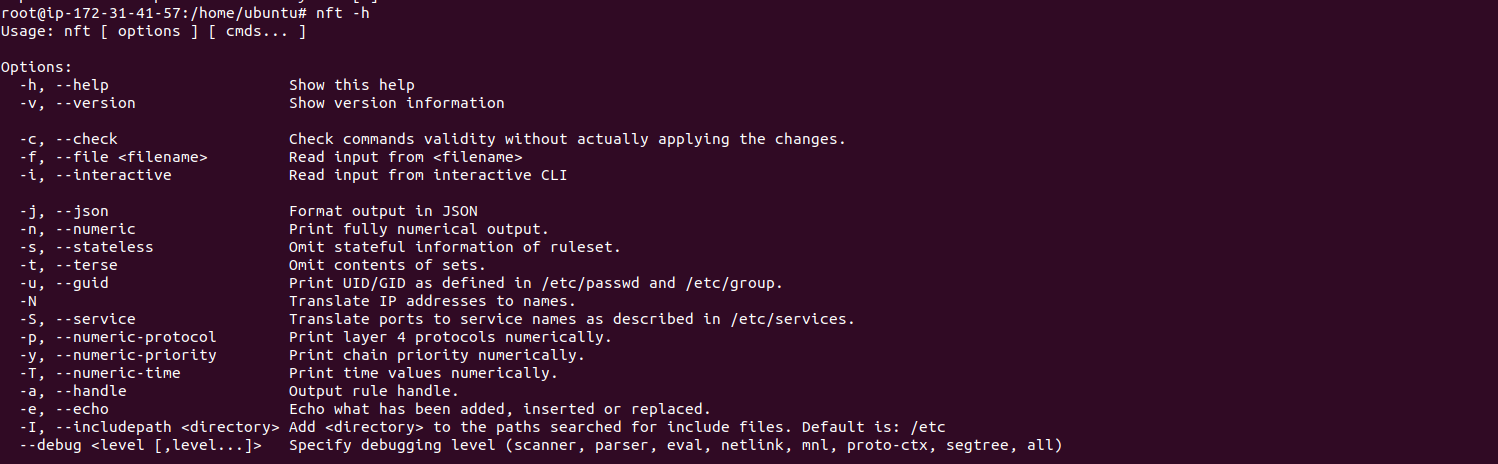
How To Install Nftables On Ubuntu 2004 Lts

Using Nftables On Oracle Linux 8 - Youtube
Nftables 1 Nftables Installation - Computer Outlines Blog
Netfilter Iptablesiptablesnft-sharedh File Reference