Nft Add Table Inet Filter
# nft add table ip filter; } nft create chain inet filter forward {.

Using Nftables On Oracle Linux 8 - Youtube
Nft add table inet table_name nft add table inet filter nft add table inet example_tables.

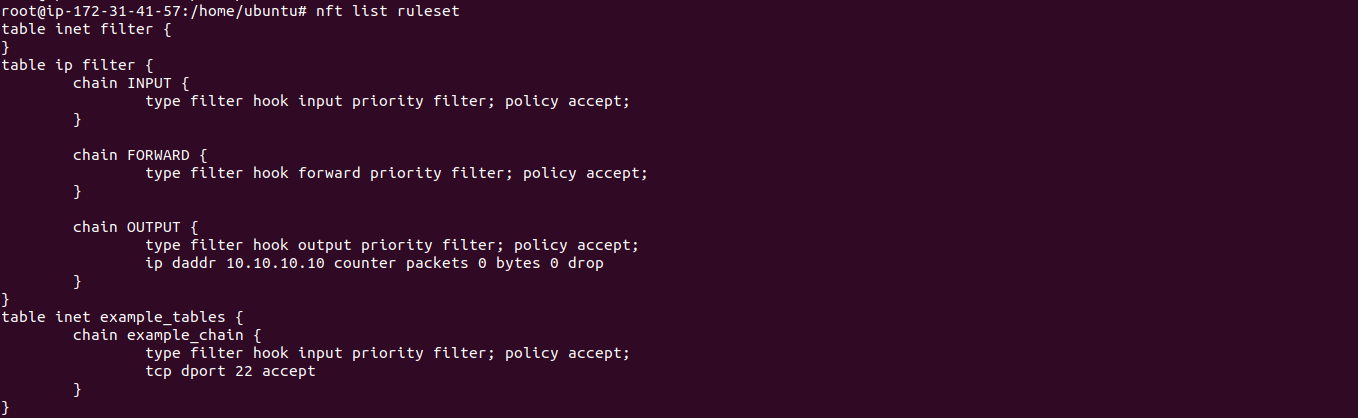
Nft add table inet filter. # nft list table inet filter table inet filter { } Root@host:~# nft insert rule ip filter input position 17 iifname eth0 ip saddr { 192.168.1.11, 192.168.1.68, 192.168.1.118 } counter drop nat create table root@host:~# nft add table ip nat create chains. Now to give higher priority to forward chain of filter table assign priority less than 0.
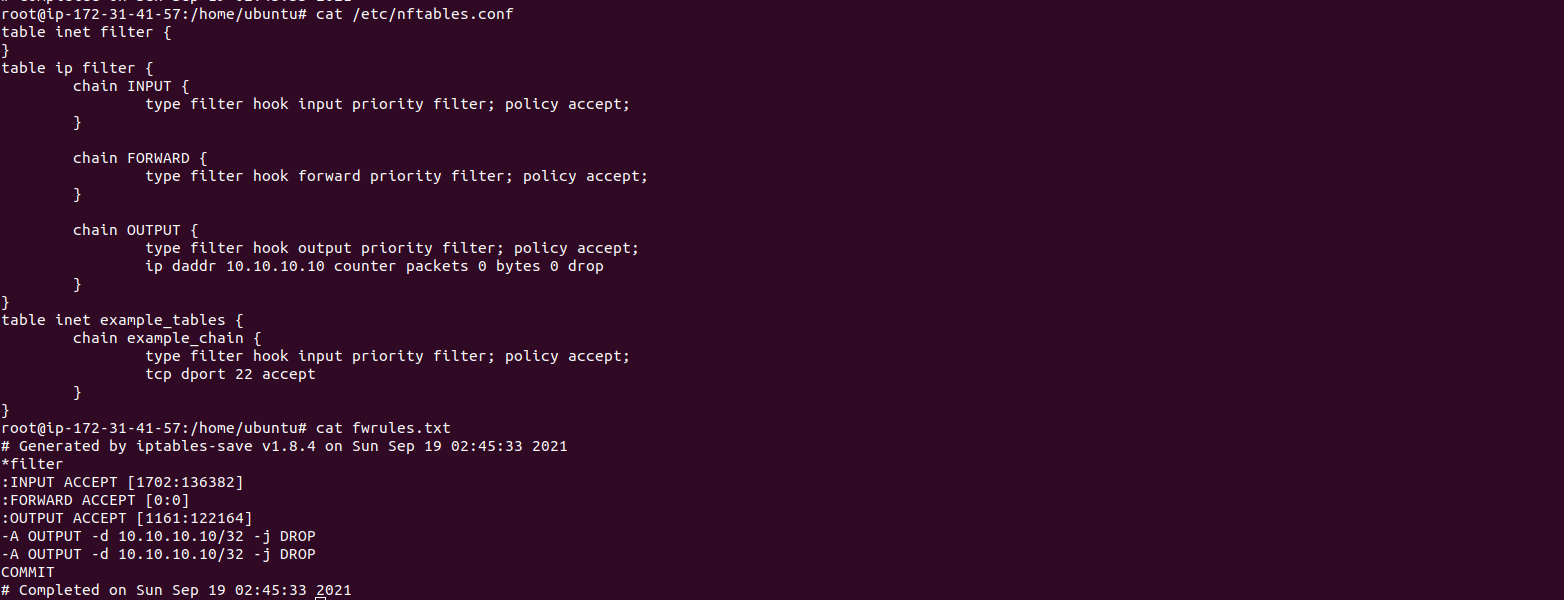
Sudo nft add chain inet filter input \{ type filter hook input priority 0 \; And it was saved right in place/ 4. Here is the command output.
Sudo nft list ruleset > /etc/nftables.conf. Root@host [~]# nft add rule inet. Policy accept \} #add a new rule, to accept several tcp ports:
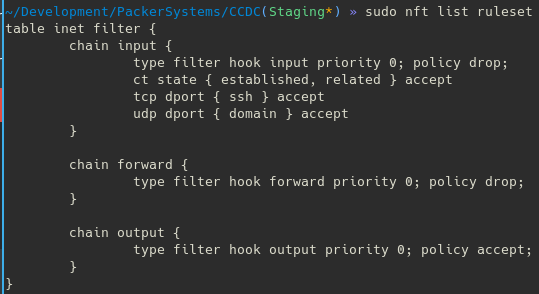
Ct state invalid counter drop comment early drop of invalid packets ct state {established, related} counter accept comment accept all connections. # nft add table inet filter # nft list tables table inet filter. Sudo nft add table inet filter;
This will work (once you get a recent enough nftables): Get input packets add chain inet mytable myin { type filter hook input priority 0; To create a new table below the inet family:
} this command creates a dynamic set for ipv4 addresses. Nft add table inet filter. Root@host:~# nft add chain ip nat my_masquerade '{ type nat hook postrouting priority 100;
}' add a rule to the chain for counting packets destined for 8.8.8.8. Inet has been available since kernel 3.14. Nft create chain inet { type filter hook < (input|forward|output)> priority 0 \;
Policy accept \} add a new rule to accept several tcp ports: Add the input chain to the filter table: Nft add table inet filter and so on 3.
Nft create chain inet filter input { type filter hook input priority 0 \; } add a set named denylist to the filter table: # nft add set ip filter denylist { type ipv4_addr \;
This script will create a new nftables table, so make sure the provided table name is unique and not being used by any other table in the ruleset. Syntax for creating base chains: The equivalent hooks of ipv4 and ipv6.
Add a new table, with family “inet”. Take care if rules are contained in more than one table, because the tables are checked in sequence: Create table inet mytable # add a new base chain:
That's a difference with for example iptables + ipset, where the same ipset set can be used in any table. Add a new table with family inet and table filter: +nft add rule filter output ip daddr 192.168.0.0/24 accept # 'ip filter' is assumed +# same command, slightly more verbose +nft add rule ip filter output ip daddr 192.168.0.0/24 accept
Tcp dport timeout 5m limit rate 20/minute \} counter accept Root@host [~]# nft list ruleset #add a new table, with family inet and table filter: Here is the command output.
Nftables adds in addition to protocol specific tables ”ip” (ipv4) and ”ip6” (ipv6) support for a ipv4/ipv6 aware table named ”inet”. Root@host [~]# nft add table inet filter #add a new chain, to accept all inbound traffic: Root@host [~]# nft add chain inet filter input \{ type filter hook input priority 0 \;
The filter table is now created within the inet family but will be empty, it does not contain and chains: Add, change, delete a table. Nft create table ip foo nft create chain ip foo bar {type filter hook input priority 0 \;} the inet address family is special.
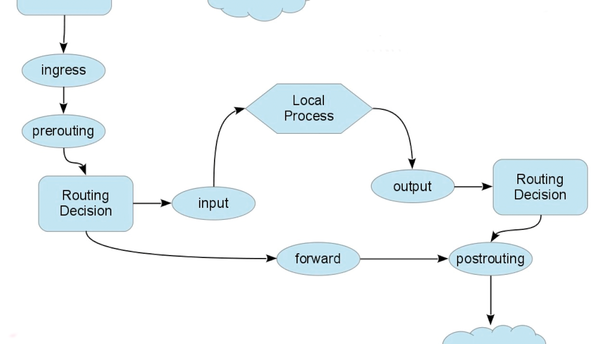
Using this table it's possible to add only one rule and match both protocols (in case of udp and tcp). When you create a table belonging to that family and then create a base chain within that table, then this base chain will get registered with two netfilter hooks: But when i reboot my nftables rules and tables dissapiered!
Add a new chain to accept all inbound traffic: # nft add chain ip filter input { type filter hook input priority 0 \;

Nftables Syntax Highlighting For Notepad Github

Using Nftables In Centos 8 And Getting Your Ready For The Rhcsa

Netfilter Framework Providing Hooks System For Nftables

Nftables Part - 2 Live Demo - Youtube
How To Install Nftables On Ubuntu 2004 Lts

Securing Your Server With Nftables Datapacketcom
How To Install Nftables On Ubuntu 2004 Lts

Additional Filters Via Nftables

Configure A Firewall With Nftables On Centos 8rhel 8 Sally Holm

Nftables Configure That Linux Firewall Like An Expert

Beginners Guide To Nftables Traffic Filtering - Linux Audit
How To Install Nftables On Ubuntu 2004 Lts

Nftables Dnat Doesnt Seem To Be Working
Firewalls How To Setup A Basic Firewall Using Ufw Iptables Nftables Or Firewalld - Angry Sysadmins
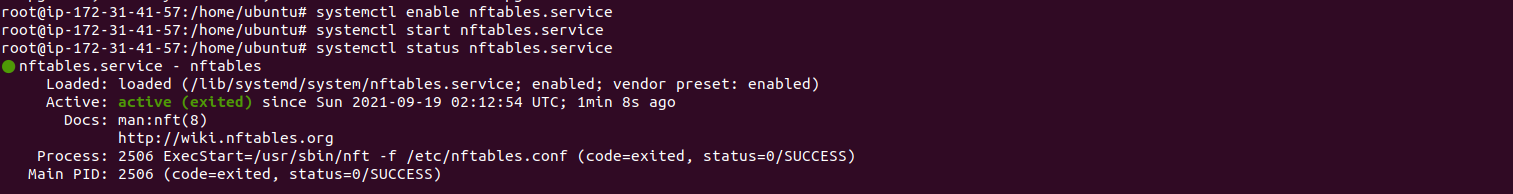
How To Install Nftables On Ubuntu 2004 Lts